Vortex
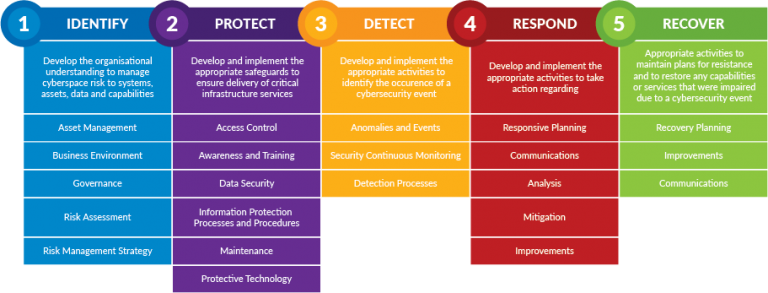
What is NIST?


Cyberstanc Vortex is an all-in-one content security solution that utilizes advanced threat detection and comprehensive file analysis to provide unparalleled protection against malware threats.
By employing cutting-edge Signature-less Detection powered by our very own Scrutiny Engine and Simulation Intelligence capabilities, Cyberstanc Vortex is able to identify and neutralize even the most sophisticated malware threats. Its advanced file analysis techniques provide a thorough examination of metadata, file structure, and relationships between files, allowing organizations to stay ahead of emerging threats.
With its “Report, Remove, and Sanitize” feature, Cyberstanc Vortex offers comprehensive protection, ensuring secure data transfer between networks. Its focus on transparency and accountability gives organizations the confidence to trust the accuracy of its results.